Why Single-Channel Security Can't Stop Modern Social Engineering
The Strategic Security Gap
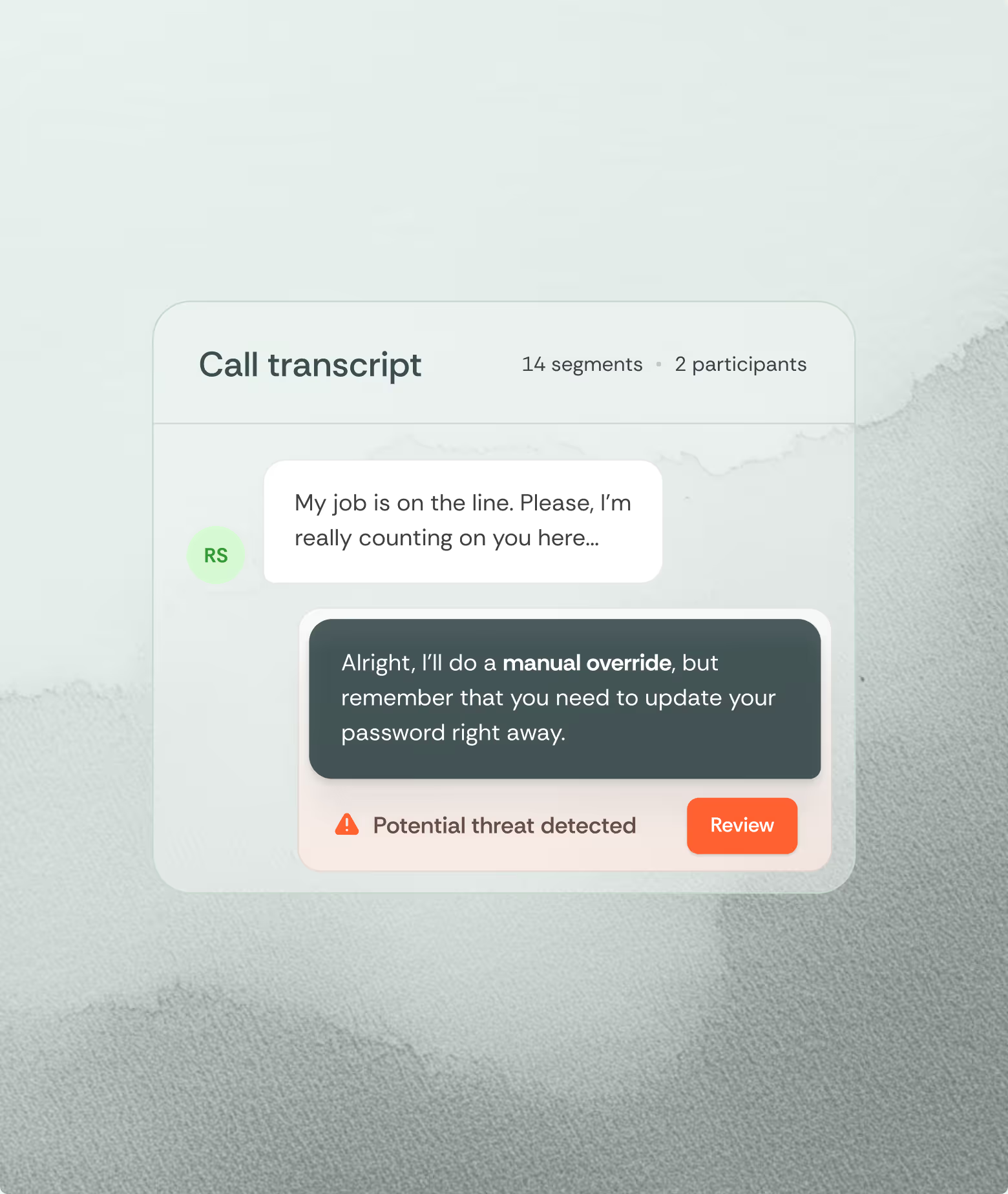
Organizations implement comprehensive network monitoring through firewalls, email gateways, and endpoint detection systems. However, human communications across voice, SMS, chat, and collaboration platforms typically operate outside these channels. When attackers coordinate deception across multiple channels simultaneously, deepfakes included, isolated single-channel defenses cannot detect coordinated campaigns.
This monitoring gap reflects security architecture priorities focused on technical infrastructure rather than human communication analysis. Organizations allocate security resources to network traffic inspection while communication channels enabling system access remain unexamined. This architectural asymmetry represents a systems failure, not an employee failure. Organizations cannot expect humans to detect sophisticated deception unaided while equipping networks with advanced threat detection.
The Business Impact
indicates average breach costs exceed $4.5 million, with social engineering attacks ranking among the most expensive incident categories. Organizations incur both direct and indirect costs. Direct costs include incident response, forensic investigation, and legal expenses. Indirect costs stem from operational disruption, productivity loss, and recovery efforts that significantly multiply total financial impact. Neither capture the erosion of trust.
Social engineering exploits normal human psychology not negligence. Employees must trust internal and external stakeholders for businesses to operate. Without detection tools analyzing conversations, even security-aware employees lack the competencies needed to identify coordinated attacks across channels.
Breach consequences extend beyond immediate remediation. Customer trust degradation, partner relationship impact, and competitive disadvantage from intellectual property theft create sustained business effects. Reputational damage persists substantially beyond technical recovery timelines.
Regulatory requirements introduce additional risks. GDPR, CCPA, and SEC rules increase the need for risk management and governance disclosures, which increases the need to demonstrate controls against material risks such as social engineering. Organizations that lack communication monitoring capabilities face difficulty demonstrating adequate security posture during audits.
The Strategic Capability Requirement
Addressing this architectural gap requires extending security monitoring to human communications with equivalent rigor currently applied to network infrastructure. Modern detection platforms utilize conversational AI to analyze conversation content across channels, identifying manipulation tactics including authority exploitation, urgency fabrication, and deception indicators.
These capabilities integrate with existing security infrastructure through SIEM platform connectivity, enabling correlation with authentication logs, access control events, and incident response workflows. Beyond breach prevention, conversational AI identifies policy-practice misalignments, enabling targeted improvements to processes and security awareness training.
Organizations that implement human communication monitoring capabilities equivalent to network traffic analysis address critical architectural vulnerabilities. As generative AI technologies enable increasingly sophisticated impersonation attacks, comprehensive communication monitoring represents essential security infrastructure rather than optional capability enhancement.
Recommended Actions
Strategic Assessment. Conduct comprehensive evaluation of current human communication monitoring capabilities across all channels. Identify and quantify monitoring coverage gaps. Present findings to executive leadership documenting architectural risk and business impact.
Business Case Development. Calculate potential breach cost exposure using industry benchmarks and organizational risk profile. Compare detection capability investment requirements against projected avoided loss. Utilize Return on Security Investment (RoSI) frameworks for financial analysis.
Compliance Review. Evaluate regulatory requirements relevant to organizational operations (NIST Cybersecurity Framework, ISO 27001, industry-specific mandates). Document compliance gaps related to social engineering controls. Define how human threat detection and response capabilities address regulatory obligations.
Pilot Program Implementation. Deploy initial monitoring capabilities for high-risk organizational functions including IT support, financial operations, and executive communications. Establish quantifiable success metrics including detection rate, false positive reduction, and prevented incident documentation.