Detecting Reconnaissance and Deceptive Pretexting Before Attacks Begin

The Invisible Preparation Phase
Every successful social engineering attack begins with reconnaissance. Attackers gather intelligence about your organization, employees, and processes before contact.
We often fail to realize the amount of information they post online about people and processes. Attackers scrape LinkedIn for organizational charts, monitor press releases, and study job postings. They find executive interviews and articles, employee’s social media, and other records - each provides a piece of the puzzle. AI can accelerate this process.
The information asymmetry allows attackers to know enough to seem legitimate. But they lack deep insider knowledge. This is their weakness.
Reconnaissance typically occurs outside your perimeter through OSINT, making direct detection impossible. However, the pretexting attempts that follow create observable patterns. If we follow this trail, we can stop social engineering.
Pretexting Patterns That Reveal Reconnaissance
Information asymmetry exposes impersonation. Attackers possess surface details from reconnaissance but lack the contextual knowledge of legitimate employees. The "executive" who knows company initiatives but not their direct reports' names. The "vendor" citing project names but unaware of contract specifics. The "traveling employee" with correct manager information but wrong departmental processes. Legitimate employees have rich mental models about processes and timelines that are not available to others. These gaps reveal reconnaissance-based attacks.
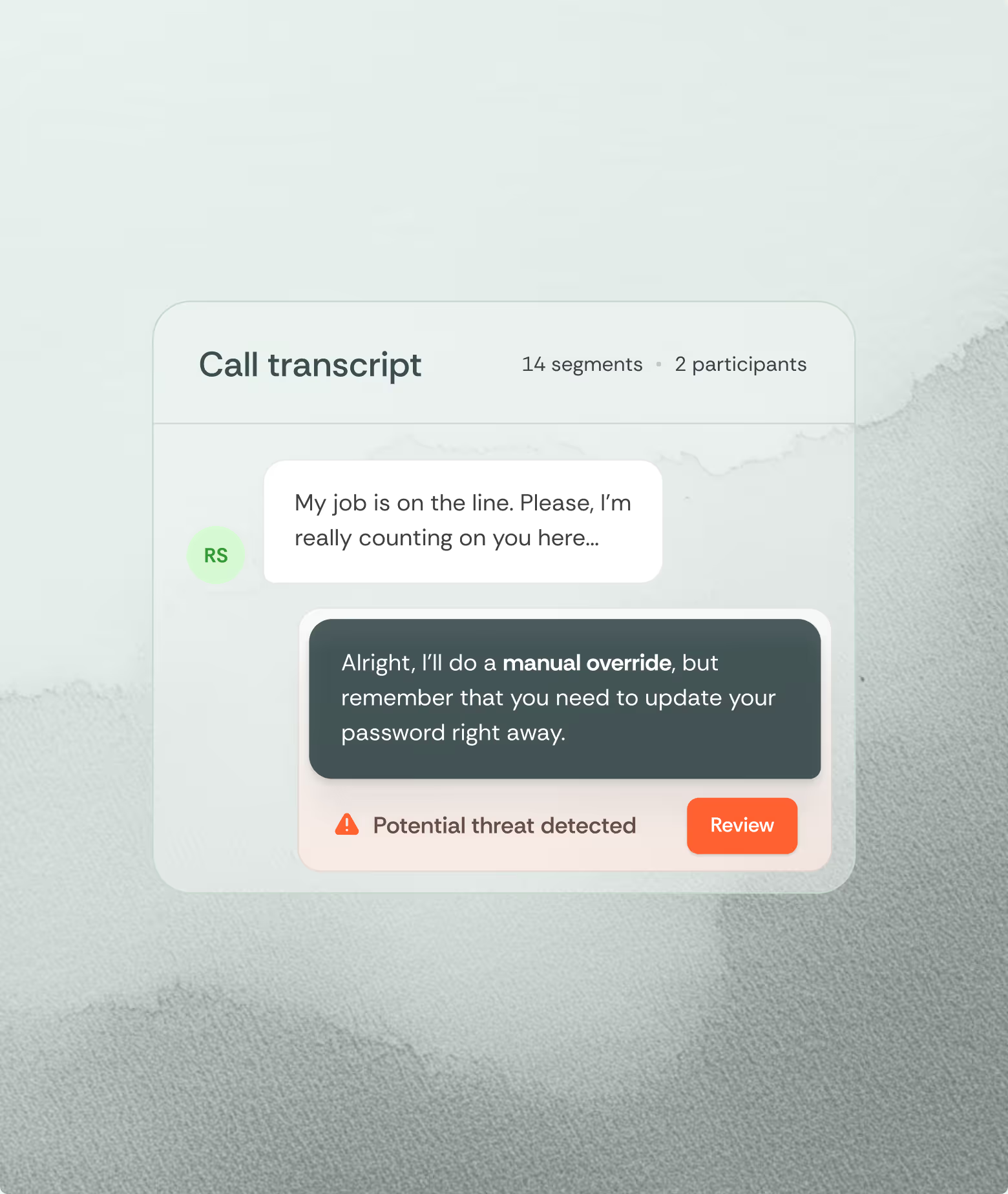
Legitimate users might not be happy, but they rarely resist verification. Attackers have no other choice. They craft elaborate explanations for why standard authentication won't work: lost phones, system issues, and travel complications are bountiful. They've researched enough to know verification will fail, so they prepare justifications to side-step it.
Probing behavior reveals information gathering through questions about procedures, calls mapping approval processes, contacts testing responses. Questions about password reset procedures disguised as policy clarification. Calls to multiple departments mapping approval processes. These reconnaissance contacts precede actual attacks by days or weeks, providing early warning if detected. They can be easily missed.
Temporal patterns expose campaigns: first-time callers requesting immediate access, multiple similar contacts, off-hours requests. Requests during off-hours when verification is difficult. These timing anomalies, especially from unknown contacts, signal potential reconnaissance or pretexting.
Building Early Detection Capabilities
Help your help desk build resiliency. Make it a part of your organizational culture and adopt technologies that support it.
Document external contacts with security-sensitive functions: caller details, stated purpose, information requested, verification outcomes. This contact history reveals patterns invisible to individual interactions. When multiple employees receive similar probing calls, that’s active reconnaissance.
Establish knowledge benchmarks by role. Define what information legitimate executives, vendors, and employees should possess. When callers fail these knowledge checks despite having partial information, you've detected reconnaissance-based impersonation.
Deploy conversation analysis tools that identify pretexting language patterns. Excessive detail in backstories, scripted responses to challenges, and reluctance to provide callback numbers all indicate prepared deception. Real-time analysis can flag these patterns during active calls.
Correlate failed verifications with attacks. Password resets following multiple failed attempts indicate reconnaissance-enabled social engineering.
Recommended Actions
Immediate steps: Log all help desk verification failures and bypass requests. Alert on first-time callers requesting sensitive actions.
Prevention focus: Share detected pretexting attempts organization-wide. When employees know current attack narratives, they become immune to those specific pretexts.
Reconnaissance and pretexting represent the attack phases where detection costs least and prevents most. Organizations that identify these early indicators stop attacks before compromise—the difference between investigation and breach.
Implementation resources:
- MITRE ATT&CK reconnaissance techniques (T1598, T1593, T1589)
- OSINT framework for understanding attacker reconnaissance methods
- Social Engineering Toolkit documentation for pretext examples
- Human Threat Detection and Response platforms for conversation analysis
- Industry Information Sharing and Analysis Centers (ISACs) for active campaign intelligence