Implementing Cross-Channel Correlation for Social Engineering Detection
Multi-Channel Attack Patterns
Although some breaches are the result of carelessness, social engineering often requires skill. Successful social engineers fragment operations across channels to evade single-channel detection. Typical sequences progress from email contact to voice urgency escalation to SMS authentication bypass. Each appears legitimate in isolation. Together, temporal correlation reveals systematic coordination.
Technical indicators include authentication attempts from new locations following help desk calls, multiple MFA prompts after voice interactions, and command-line execution following support site visits. When coupled with social engineering cues, these technical signals indicate that a coordinated breach attempt.
Implementation Architecture
Comprehensive cross-channel detection requires four technical components: unified data collection, conversational content analysis, a correlation rule engine, and a behavioral baseline system.
Data Collection Infrastructure. Aggregate communication logs from all channels: email (headers, content, attachments), voice (call records, transcripts, audio, deepfake detection), SMS (content, sender data), and collaboration platforms (activity, messages, files).
Conversational Content Analysis. Deploy speech-to-text and natural language processing to analyze conversation content, not just metadata. LLM-based systems identify policy violations (authentication bypasses, approval circumventions), manipulation techniques and procedures (urgency language, authority claims), and information asymmetry (surface knowledge without insider context). Content analysis output feeds correlation engine alongside metadata, enabling detection of manipulation tactics spanning channels even when temporal patterns appear normal.
Correlation Rule Development. Implement SIEM rules identifying multi-channel sequences such as email followed by voice within 30-minute windows. Advanced rules match topics across channels (account names, projects, deadlines) and flag authentication events following communications. Conversational analysis output feeds correlation rules, with linguistic indicators and temporal patterns combined to produce escalated alert priorities.
Behavioral Baseline Establishment. Deploy UEBA to establish normal communication patterns by role focusing on channel usage, contact frequency, and interaction timing. Deviations trigger investigation, especially when coinciding with authentication or access events.
Detection Rule Examples
Sequential Contact Detection. Alert when individual users receive email followed by voice call from same claimed identity within 60 minutes, particularly when communication references account issues, password problems, or access requirements.
Cross-Channel Topic Matching. Flag communications across different channels mentioning identical project names, deadlines, or account identifiers within compressed timeframes, indicating potential coordinated campaign activity.
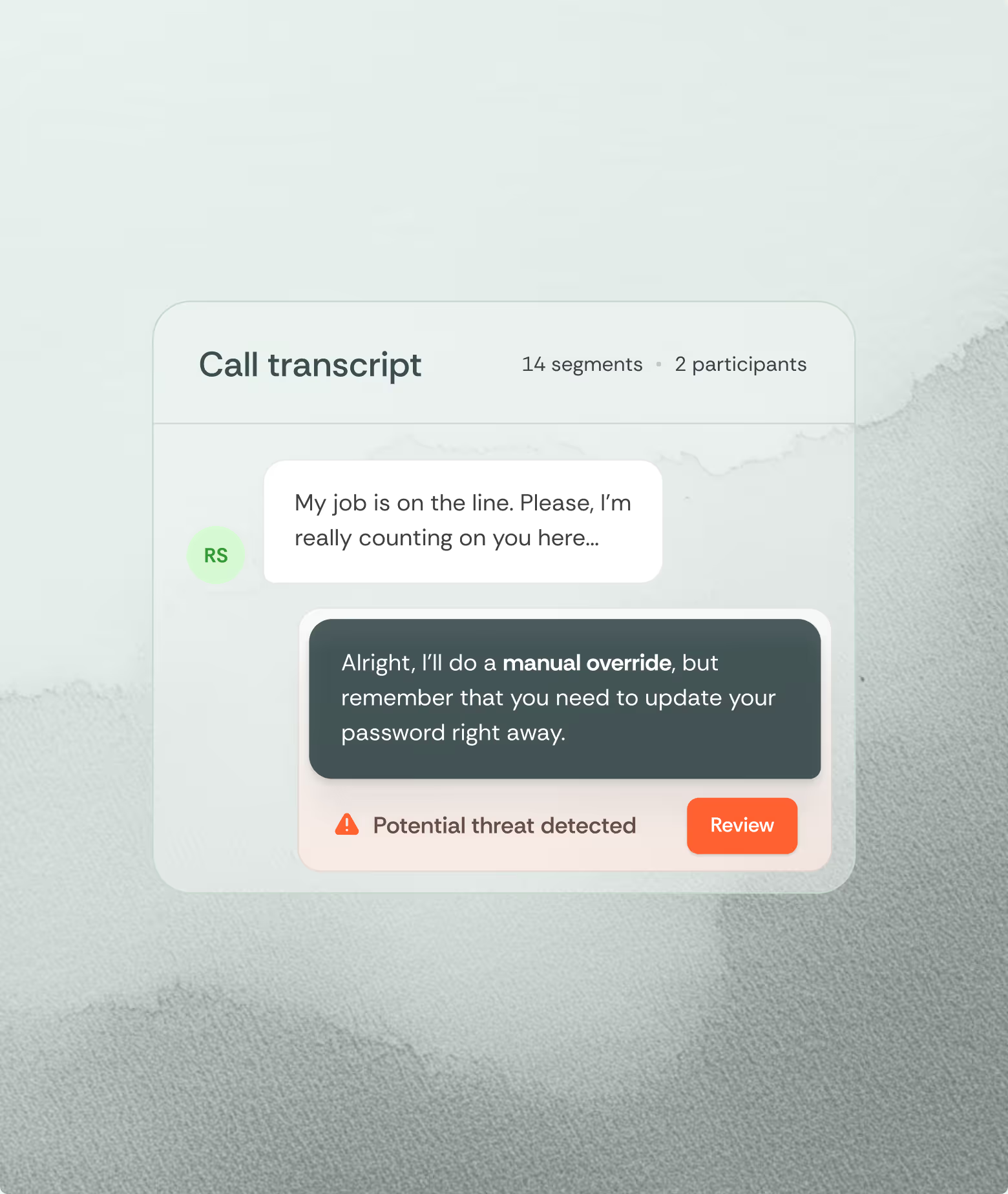
Content-Behavioral Correlation. Alert when urgent language in email ("immediate action required") is followed by voice call within a brief period using similar phrasing, especially when requesting policy exceptions. Content consistency across channels indicates coordinated manipulation.
Authentication Correlation. Generate high-priority alerts when help desk interactions precede authentication failures, password reset requests, or privilege escalation attempts within 24-hour windows.
Cross-channel detection transforms isolated communication monitoring into comprehensive attack pattern identification, enabling security operations to detect coordinated social engineering campaigns before unauthorized access occurs.
Recommended Actions
Phase 1. Audit communication channel logging completeness. Identify gaps in voice recording, SMS retention, and collaboration platform monitoring. Implement missing data collection.
Phase 2. Configure SIEM to ingest communication logs from all channels. Develop basic correlation rules for sequential contact patterns and authentication timing.
Phase 3. Deploy conversational AI to analyze communication content for social engineering indicators. Implement LLM-based detection of manipulation tactics, urgency language, and policy circumvention attempts across voice, email, and messaging channels.
Phase 4. Deploy UEBA baselines for high-risk roles including IT support, financial operations, and executive functions. Establish deviation thresholds triggering review.
Phase 5. Integrate detection alerts with incident response through SOAR automation. Define escalation procedures and investigation playbooks for confirmed social engineering attempts.
Why Help Desks Become Attack Targets
Help desks consolidate extraordinary access authority. Every password reset, MFA bypass, and privilege escalation flows through this single function. Attackers recognize this concentration of power and target help desk agents who face two competing priorities: to resolve issues quickly and to follow security protocols.
Social engineers exploit these operational pressures through calculated pretexting. They claim that a device was lost during travel, reference urgent deadlines that prevent standard verification, or impersonate vendors needing immediate system access. Social engineers understand help desk performance metrics prioritize resolution speed and customer satisfaction, creating exploitable gaps between security policy and actual practice. The faster the transaction, the more likely critical steps will be bypassed.
Voice interactions particularly favor attackers because they enable real-time adaptation. When verification challenges arise, skilled social engineers pivot immediately, providing partial information to seem legitimate while claiming special circumstances prevent full authentication. They read an agent’s responses and adjust emotional tone and urgency levels to maximize compliance probability.
Building Help Desk Defense Capabilities
Start by instrumenting all help desk communications. Log interaction metadata (caller information, request types, verification attempts, resolution actions) and integrate with your SIEM platform. Call recording and transcription enable pattern analysis for social engineering attempts across multiple interactions.
Establish behavioral baselines for typical requests by department and role. When accounts that normally self-service suddenly need help desk assistance, or when simple requests become complex multi-step changes, enhanced verification should trigger automatically. These baselines reveal anomalies that individual agents might miss.
Real-time conversation analysis through Human Threat Detection and Response platforms can identify manipulation tactics during active calls. These systems flag high-risk language patterns, emotional manipulation, and verification avoidance, alerting supervisors before agents complete dangerous requests.
Create correlation rules linking help desk activity with other security events. When password reset requests follow failed login attempts, phishing emails, or account reconnaissance, your detection systems should escalate immediately. These connections reveal coordinated attacks invisible to help desk agents.
Help desks remain attractive targets because they control organizational access. Security teams that monitor help desk interactions with the same rigor applied to authentication systems detect and prevent social engineering before compromise occurs.
Recommended Actions
Immediate steps: Audit current help desk logging completeness. Create SIEM alerts for failed verifications, unusual request combinations, and changes to privileged accounts. Assess whether your current Human Threat Detection and Response capabilities are adequate.
Critical process change: Implement mandatory verification escalation for sensitive requests: supervisor approval for privilege changes, callback requirements for executive accounts, and time delays for suspicious request patterns.
Implementation resources:
- NIST SP 800-63 (Digital Identity Guidelines) for verification standards
- SANS SEC504 incident handling and attacker techniques
- ITIL Service Desk security integration guidelines
- Human Threat Detection and Response tools for conversation analysis
- Industry frameworks for help desk security controls