Authority and Urgency in Social Engineering Attacks

The Compliance Formula: Authority Plus Urgency
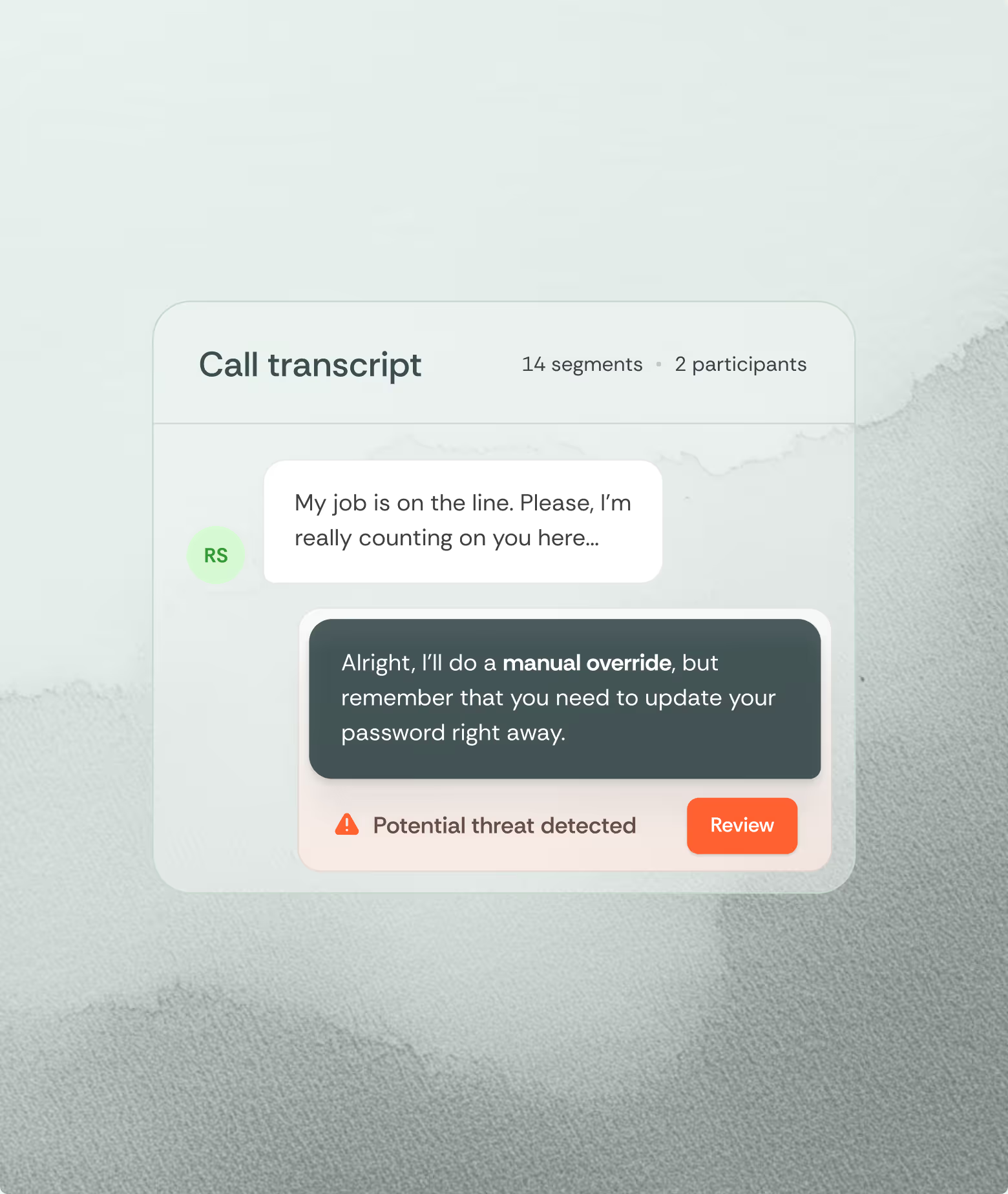
Social engineers exploit a fundamental truth: authority and urgency create compliance pressure. When someone claiming executive status demands immediate action (”Give Gary access.”), employees must choose between security procedures or obeying leadership under time pressure. Attackers know which motivation wins.
Authority manipulation works because it exploits organizational hierarchy through impersonating executives, board members, or external authorities. Employees defer to high-status individuals, knowing that questioning authority risks career consequences. Attackers need only convincing credentials, project knowledge, or confident delivery.
Creating a sense of urgency narrows decision-making. Attackers create artificial deadlines, threaten consequences, or claim emergencies. Time pressure induces cognitive tunneling where employees solve immediate problems rather than considering context. Urgency increases fear and anxiety overrides security training when organizational cultures rewards action.
Combined, these tactics create maximum manipulation: the "executive" needing emergency wire transfers, the "IT director" requiring immediate password resets, the "auditor" demanding documents before deadlines.
Detection Patterns in Authority and Urgency Exploitation
Linguistic analysis reveals manipulation in real-time. Authority claims include title declarations ("This is the CFO"), name-dropping ("Mrs. Lee authorized this"), hierarchy references. Urgency markers include time constraints ("needed immediately"), consequence threats, pressure phrases ("just this once"). Natural language processing flags these patterns during communications.
Behavioral inconsistencies expose impersonation. Real executives know direct reports, understand internal processes, follow established procedures under pressure. Attackers lack contextual knowledge—the "CEO" unfamiliar with the CFO's name, the "IT director" unaware of change control. These gaps reveal deception despite convincing authority claims.
Timing anomalies suggest manipulation: after-hours urgent requests from executives working standard schedules, first-time callers claiming authority, urgent demands following failed authentication.
Verification resistance signals deception. Legitimate authority accepts security procedures. Attackers resist—claiming urgency prevents verification, refusing established authentication, showing anger when challenged.
Building Real-Time Detection and Response
Deploy conversation analysis tools identifying manipulation patterns during active communications. Modern system should flag authority invocations, urgency escalation, and verification avoidance in real-time.
Establish verification protocols applying regardless of claimed authority or urgency. Out-of-band confirmation, callback requirements, mandatory cooling-off periods prevent impulsive compliance.
Create behavioral baselines for sensitive positions and executive roles. When claimed authorities deviate from established communication patterns, enhanced verification automatically triggers.
Recommended Actions
Immediate steps: Alert on authority claims combined with urgency language. Require supervisor approval for urgent executive requests.
Cultural consideration: Make it safe for employees to verify authority without career consequences. No detection system works if employees fear challenging executives more than breaches.
Implementation resources:
- Robert Cialdini's
- NIST SP 800-50 on security awareness training
- FBI IC3 Business Email Compromise reports
- Human Threat Detection and Response platforms