Detect and respond to attacks on humans
Most breaches begin with people, not systems.
Connected where people communicate
Humanix securely ingests human interactions and contextual activity via API — while working seamlessly alongside your people’s existing workflows.
Multi-channel, multi-modal interaction analysis
Humanix analyzes human interactions across voice, chat, email, and service channels, correlating single- and multi-channel attacks into easy-to-understand attack timelines.


Easy integration with the tools your people already use
Humanix securely analyzes data from the systems your teams already use for communicating with customers, employees, and partners. You retain continuous control over your own data.
Protecting people across every interaction
Humanix uses conversational AI trained on human psychology to assess, detect, respond, and assure all interactions across the enterprise.
Understand your human attack surface
Ensure your third or first party service functions follow correct policies, every time. Continuously monitor interactions for alignment with organizational policies and procedures. Upload your own policies and procedures, or leverage industry standards.

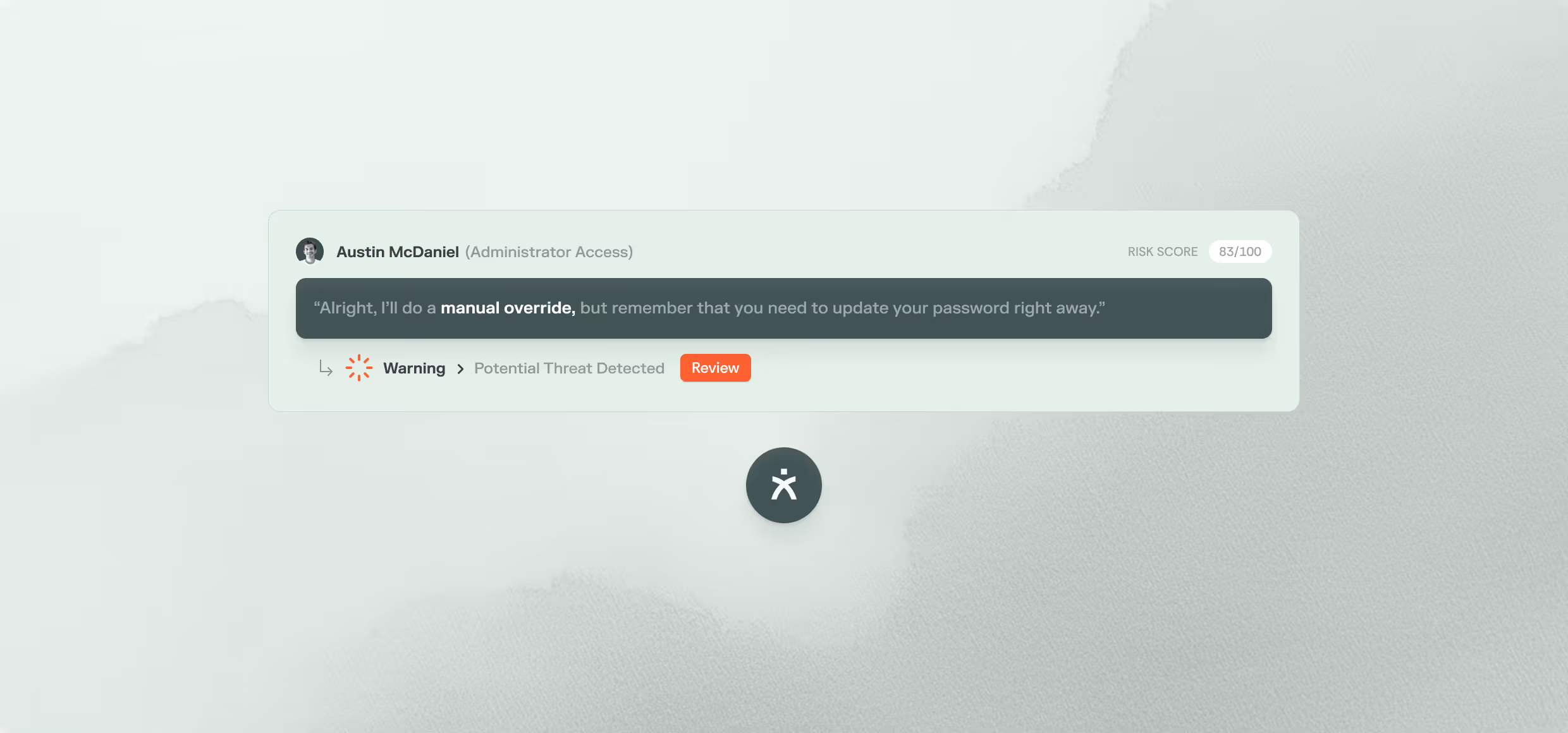
Identify attacks on humans with precision
Detect natural language attacks. Fine-tuned AI models detect linguistic and psychological indicators of persuasion, deception, and impersonation. Humanix correlates language cues, relationship context, and policy data across channels to identify real attacks.

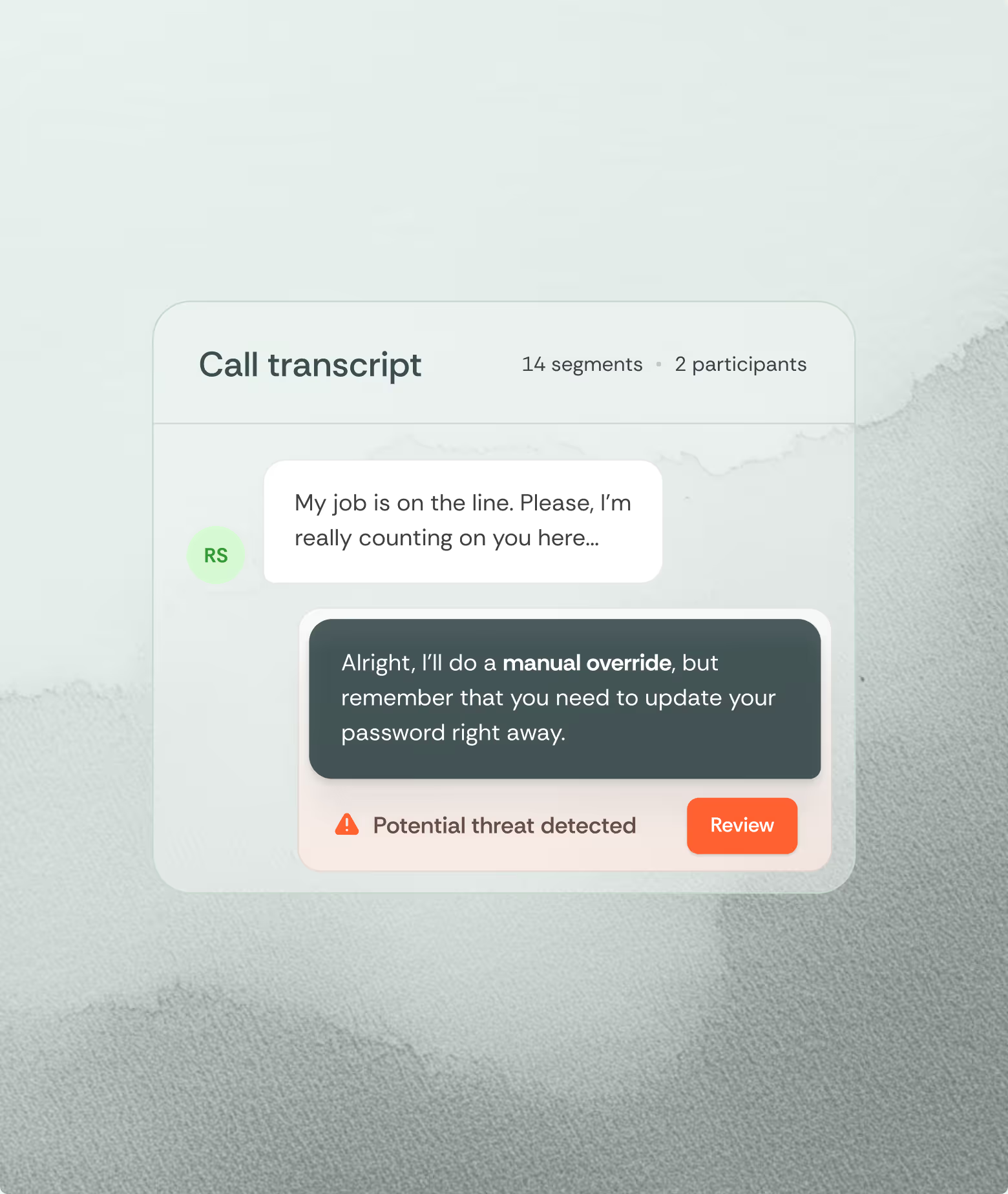
Stop active attacks before damage
Remediate human threats. Humanix alerts analysts in their native tools, and supports them with recommended actions like 'verify identity' or 'disable account.'

Continuous monitoring for policy alignment
Ensure your third or first party service functions follow correct policies, every time. Continuously monitor interactions for alignment with organizational policies and procedures. Upload your own policies and procedures, or leverage industry standards.

See results in moments,
not months
Humanix rapidly analyzes current and historical data to identify security incidents and points of vulnerability across your human layer.
Detect social engineering attacks
Alert your SOC (and perhaps the victim) to attacks as they happen.

Identify policy and procedure violations
Pinpoint behaviors that expose the organization to risk, and recommend responses or interventions.
Demonstrate and assure compliance
Provide observability and objective evidence that first and third party teams are in compliance with commitments.