How Your Employees' Good Instincts Can Become Security Vulnerabilities

Why Human Behavior Becomes the Attack Vector
Social engineering succeeds by exploiting predictable human responses such as trust in authority, urgency under pressure, and cooperation with colleagues. Traditional security controls must monitor technical indicators while attackers manipulate human decision-making. Effective detection requires understanding cognitive patterns that create vulnerability and building systems that identify exploitation attempts in real-time.
Employees make thousands of micro-decisions daily - which requests to approve, which callers to assist, which emails to trust. Under cognitive load, our mind relies on shortcuts: recognizing patterns, trusting authority, cooperating with urgency. This mental efficiency enables productivity but creates exploitable vulnerabilities.
Social engineers recognize these patterns as system vulnerabilities. They know people trust familiar patterns, defer to authority under pressure, and prioritize helping over verification. When performance metrics demand speed, verification steps get skipped. Traditional security tools miss these attacks entirely: firewalls cannot detect emotional manipulation, and endpoint protection cannot flag authority exploitation.
Behavioral Patterns That Reveal Manipulation
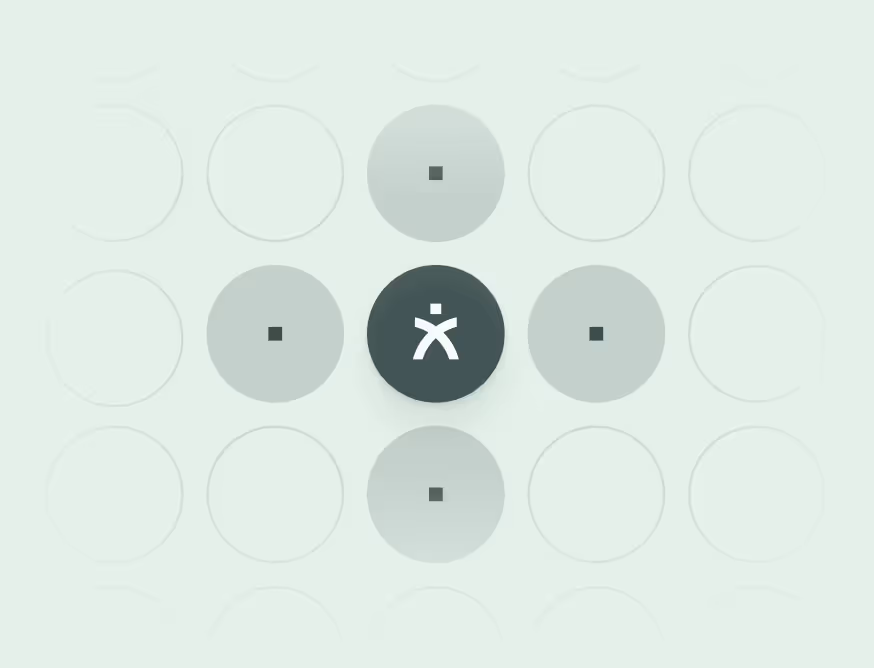
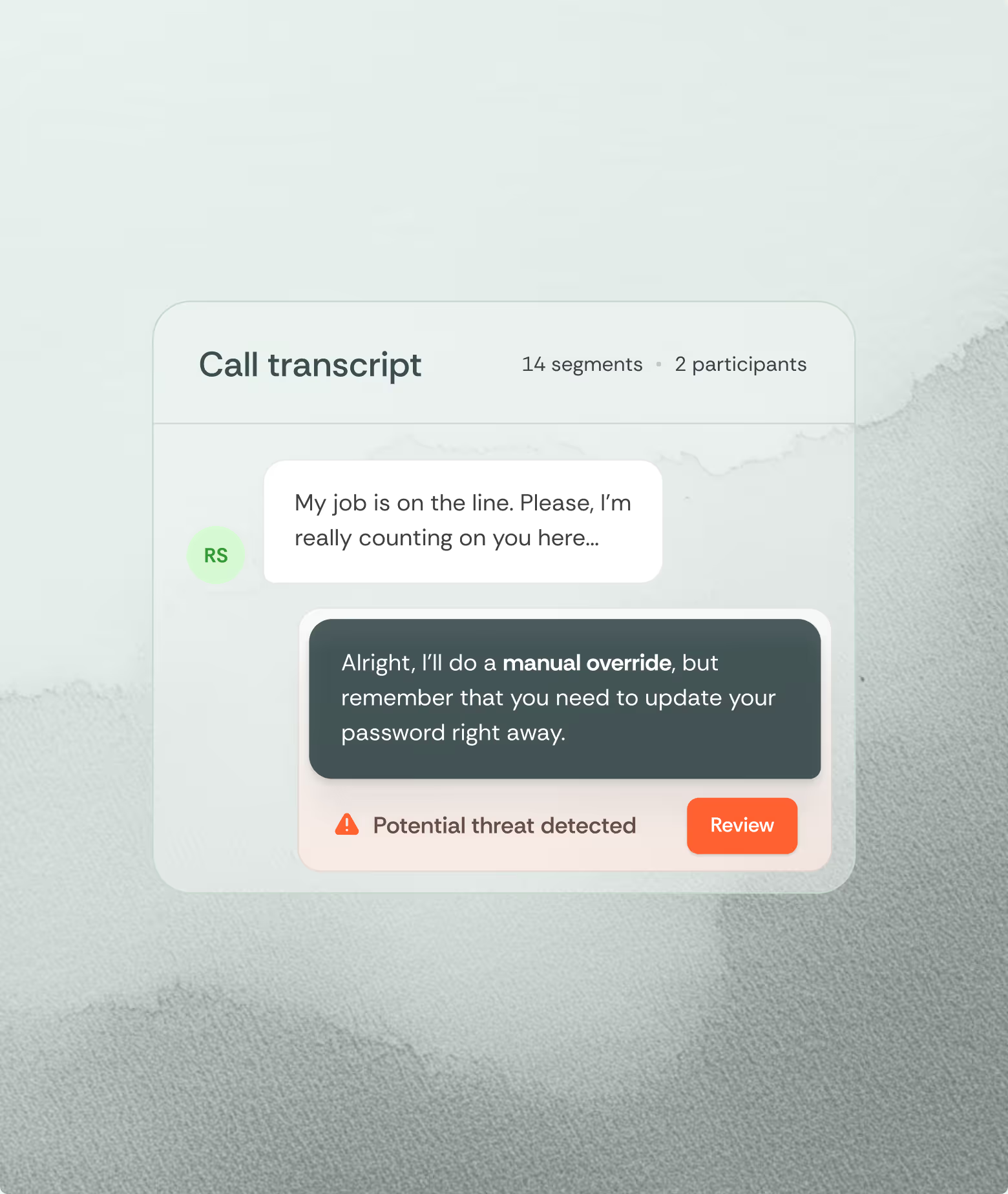
Manipulation attempts create detectable signatures. Requests bypassing normal verification, especially justified by urgency or authority, indicate potential exploitation. Quarter-end deadlines, executive requests, and customer emergencies become vulnerable decision points.
Communication patterns expose manipulation. Multiple simultaneous contacts across channels overwhelm cognitive capacity. Sequential interactions building trust through small requests before major asks follow documented influence techniques. Unnecessary urgency, sympathy appeals, and fear indicators signal social engineering.
Timing anomalies suggest exploitation of operational rhythms. Attacks cluster around high-pressure periods when vigilance drops - attackers understand organizational psychology and time their manipulation accordingly.
Building Human-Aware Detection Systems
Effective detection monitors human communication with the same rigor applied to network traffic. Natural language processing identifies manipulation markers: urgency without justification, authority claims without verification, and emotional appeals in business context. Combined with behavioral anomalies, these linguistic patterns define exploitation attempts.
Context correlation strengthens detection. When unusual communication patterns coincide with authentication attempts, privilege requests, or payment processing, the combination signals active manipulation. Behavioral baselines by role and department distinguish legitimate urgency from manufactured pressure.
Real-time decision support helps employees under attack. Human Threat Detection and Response systems analyze ongoing conversations using NLP to detect urgency clustering, authority stacking, and emotional manipulation, prompting verification when exploitation patterns emerge. Rather than expecting humans to detect sophisticated deception alone, technology assists at key decision points in a process.
Critical insight. Focus detection on behavioral patterns, not individual mistakes. Create systems that support human decision-making under pressure rather than blaming human failure after compromise.
Attackers will continue exploiting human psychology because it's predictable and profitable. Organizations that monitor and support human behavior as carefully as technical infrastructure detect manipulation before it succeeds.
Recommended Actions
Immediate steps: Identify high-risk decision points where employees approve access, payments, or data sharing. Monitor communication patterns around these critical moments.
Implementation resources:
- NIST SP 800-63 guidelines on social engineering resistance
- Carnegie Mellon's Insider Threat Center behavioral indicators
- Human factors analysis frameworks from aviation safety
- Human Threat Detection and Response platforms for behavioral monitoring
- Academic research on influence techniques and resistance training