Identifying Malicious Intent in Security Policy Violations
Every day, employees bypass security controls. Most share passwords to meet deadlines, skip approval processes during emergencies, or disable safeguards that slow critical work. But hidden among these operational workarounds, attackers exploit the same gaps. One violation helps the business, the other enables breach. Your detection systems must distinguish between them.
The Dangerous Ambiguity of Policy Violations
Security teams face an uncomfortable truth: strict compliance would bring business operations to a halt. Employees develop workarounds because policies often conflict with operational reality. These informal processes become organizational knowledge. Everyone knows which approvals can wait, which verifications to skip during crunch time, which shared accounts exist despite policy.
Attackers study these patterns. Through reconnaissance and social engineering, they discover which controls employees routinely bypass. They craft attacks that mimic legitimate workarounds, knowing security teams hesitate to flag familiar violations.
The challenge isn't detecting policy violations. It’s determining intent when the same action could indicate helpfulness or harm.
Effective detection requires behavioral context that distinguishes operational necessity from malicious exploitation.
Patterns That Reveal Malicious Intent
Malicious policy violations create distinct patterns when aggregated. Violation progression provides the clearest signal. Attackers test boundaries incrementally, starting with minor bypasses before major exploitation. Employees seeking efficiency maintain consistent workaround patterns while attackers escalate systematically.
Timing and frequency suggest intent. Operational workarounds cluster around predictable business events such as quarterly reports, system migrations, audit preparations. Malicious violations occur opportunistically, often outside normal patterns, targeting moments of reduced oversight. Weekend access bypasses by accounts normally active only weekdays support investigation.
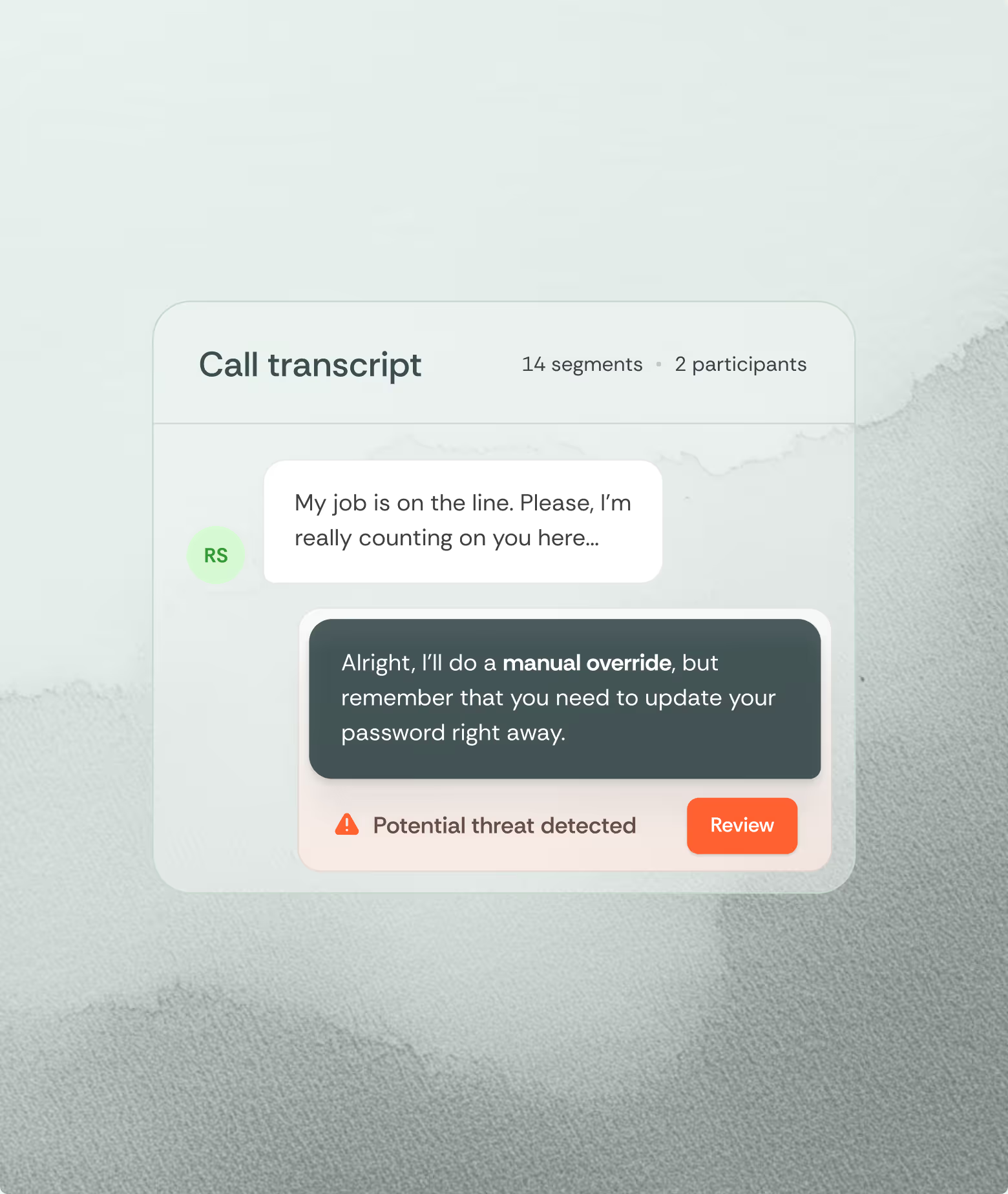
Communication context provides additional clarity. Policy violations following suspicious emails, unusual phone calls, or help desk interactions suggest social engineering. When employees suddenly use workarounds they've never needed before manipulation likely occurred.
Outcome correlation separates legitimate from malicious activity. Operational workarounds resolve tasks then cease. Malicious violations enable further compromise such as data exfiltration following access bypass, privilege escalation after authentication workaround.
Each violation represents a stepping stone rather than an endpoint.
Building Contextual Detection Capabilities
Use voice analysis to differentiate legitimate calls from those using persuasion techniques. Emergency access procedures, approval delegation systems, and shared service accounts all represent both operational realities and attack opportunities.
Use voice-based analysis methods. Recognizing normal patterns of conversation can help differentiate legitimate calls from those that use persuasion and deception techniques.
Deploy UEBA to establish violation baselines. Understanding normal workaround patterns by department and role enables detection of anomalous bypasses. When finance regularly shares credentials during month-end but engineering suddenly starts, context suggests investigation.
Correlate violations with downstream activity. Link policy bypasses with subsequent actions: data access, system changes, authentication attempts. This correlation transforms isolated violations into visible attack chains.
Strategic insight: Use detection findings to improve policy design. Frequently bypassed controls indicate friction requiring remediation. Reduce legitimate workarounds and malicious actors lose camouflage.
Policy violations will continue because perfect compliance remains operationally impossible. Organizations that analyze behavioral context can detect malicious exploitation while understanding which policies need renovation.
Recommended Actions
Immediate steps: Identify your top five most-bypassed security controls. Monitor these specifically for unusual patterns or users.
Implementation resources:
- NIST Cybersecurity Framework's "Anomalies and Events" detection guidelines
- MITRE ATT&CK framework's privilege escalation techniques
- Carnegie Mellon's insider threat detection patterns
- UEBA platforms for behavioral baseline establishment
- Industry-specific compliance violation analysis guides