How Voice-Based Attacks Bypass Your Security Controls

The Voice Channel Security Gap
Voice communication occurs in a security blindspot. While organizations meticulously scan emails and monitor network traffic, phone conversations go unexamined. Call logs capture who called when but miss the critical element of what was said and how it was said.
Social engineering can hide between these lines, with the email-voice security gap creating the perfect attack vector.
Social engineers exploit this blindspot through sophisticated manipulation. They create false urgency requiring immediate password resets. They impersonate executives demanding special access. They pose as vendors needing system credentials.
Each attack succeeds because no security tool analyzes the conversation itself, where deception occurs.
Voice calls demand immediate responses, preventing verification. Skilled attackers read hesitation, adapt instantly, and pivot between pretexts until they find what works.
Detecting Deception in Real-Time Conversations
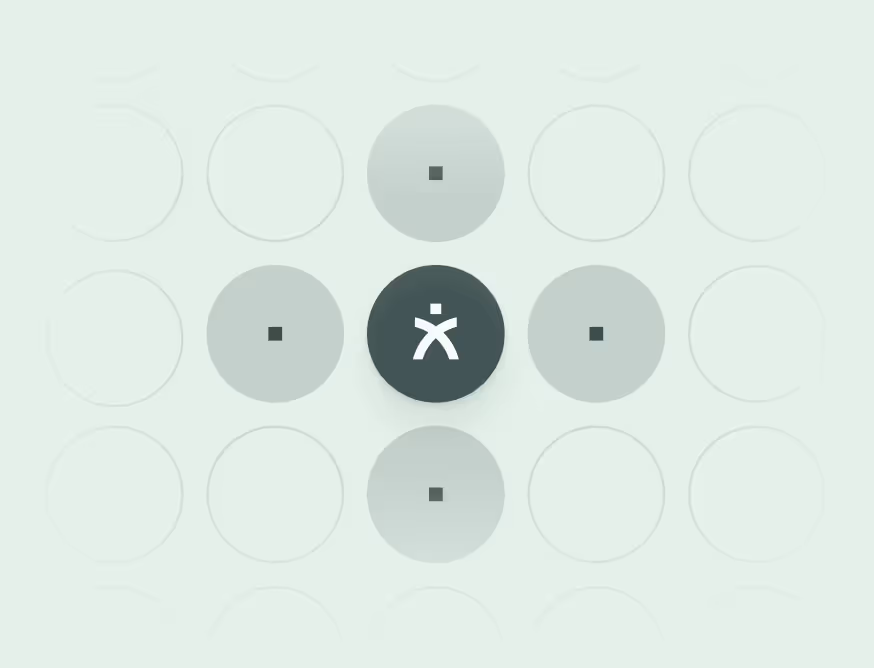
Voice attacks create detectable patterns: policy violation requests. Emergency password resets, MFA bypasses, and privilege escalations often come wrapped in elaborate explanations why normal procedures cannot apply.
Identity inconsistencies reveal pretexting attempts. When claimed executives unfamiliar with basic company terminology, or supposed vendors cannot reference actual contract details, you're likely hearing rehearsed scripts rather than legitimate callers. Attackers possess surface knowledge from reconnaissance but lack deeper organizational understanding that emerges through natural conversation.
Behavioral patterns expose manipulation tactics. Resistance to callback verification, claims that standard authentication is unavailable, or disconnections when transferred to supervisors all indicate deception. Voice stress analysis and conversational cues can detect emotional manipulation—artificial urgency, fear appeals, or sympathy are designed to bypass rational evaluation.
Building Real-Time Voice Detection
Implement call recording for security-sensitive functions: IT help desk, service desk, legal, finance. Converting speech to text for analysis, allows for both real-time detection and post-incident investigation. This foundational visibility transforms voice from a blindspot into a monitored channel.
Deploy conversation analysis tools that evaluate both what is said and how it's said. Modern Human Threat Detection and Response platforms must analyze linguistic patterns, emotional indicators, and request anomalies during active calls. These systems alert security teams when conversations exhibit deception markers, enabling intervention before access is granted.
Integrate voice intelligence with existing security tools. SIEM correlation should immediately flag calls preceding authentication failures or suspicious logins. This integration reveals coordinated attacks invisible to isolated monitoring.
Organizations monitor every packet crossing their network but ignore conversations granting network access. Real-time voice analysis closes this gap, detecting social engineering where it actually happens—in human conversation.
Recommended Actions
Immediate steps: Enable call recording for IT support and help desk. Create basic SIEM alerts when calls precede authentication anomalies.
Implementation resources:
- NIST SP 800-53 controls for voice communication security
- SANS Voice Over IP security white papers and resources
- Human Threat Detection and Response platforms for real-time analysis
- CallMiner or Cogito for conversation intelligence
- Your existing SIEM for cross-channel correlation
Process improvements: Establish callback verification for sensitive requests. Create escalation triggers when callers resist authentication. Train staff to recognize emotional manipulation.