Developing and Implementing Cross-Channel HTDR Correlation
Why Single-Channel Monitoring Creates Blind Spots
Security architectures monitor communication channels in isolation. Email gateways scan for phishing. SMS filters block spam. Phone systems log calls. Most do not examine the content.
Each tool excels within its channel but remains blind to the others. Attackers exploit these silos deliberately, fragmenting their attacks across multiple channels to evade detection.
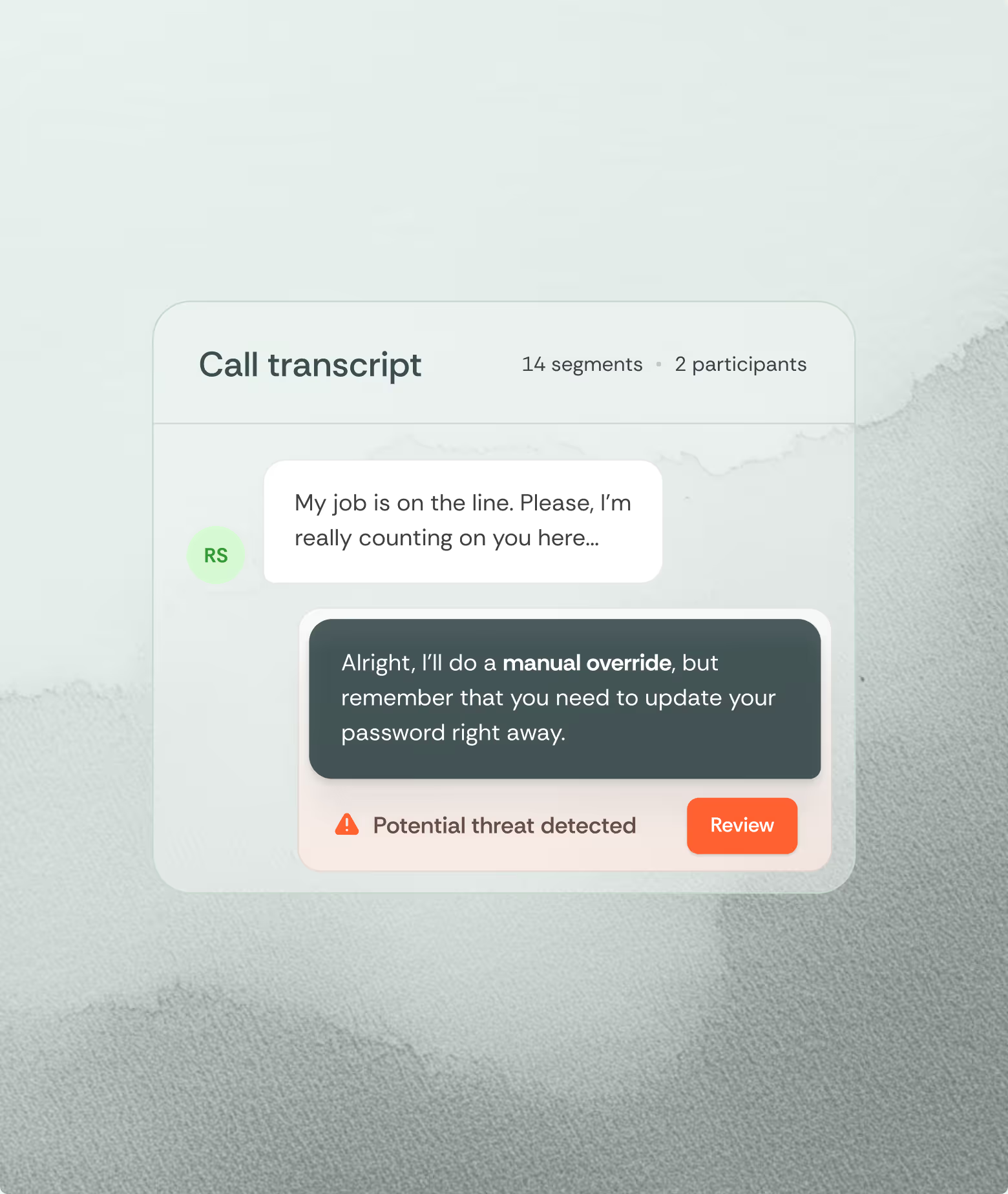
It's a playbook. Each touchpoint reinforces the others, building a narrative that seems legitimate precisely because it spans multiple channels. Security teams see fragments while attackers execute complete campaigns.
Correlation Patterns That Expose Coordinated Attacks
Cross-channel attacks create distinctive patterns. Temporal clustering- multiple channels targeting the same user within hours are the most reliable. Email, SMS, and voice converging on one individual indicates coordinated social engineering.
Content consistency across channels reveals coordination. Attackers maintain narrative coherence, referencing the same account numbers, incident tickets, or project names across different communications. Natural language processing can identify these connections, flagging when disparate channels tell the same fabricated narrative.
Behavioral patterns provide additional signals. Normal business communication rarely requires simultaneous multi-channel contact with escalating urgency. When intensity increases across channels the progression itself indicates manipulation rather than legitimate escalation.
Implementing Cross-Channel Correlation
Audit current visibility. Most organizations comprehensively log email but have minimal voice and SMS data. Language is an invaluable source of information, yet it remains largely neglected in security monitoring.
Attackers exploit these exact gaps. Complete visibility across all communication channels enables the correlation necessary to detect coordinated attacks.
Centralize communication logs in your SIEM. Normalize formats, synchronize timestamps, map identities. This enables correlation rules detecting multi-channel sequences targeting specific users.
Deploy correlation rules that flag suspicious patterns. Alert when users receive contact across three or more channels within 24 hours. Escalate when multi-channel communication precedes authentication attempts, password resets, or MFA prompts. These rules transform isolated events into visible attack campaigns.
Human Threat Detection and Response platforms purpose-built for communication analysis automate this correlation using AI to identify temporal patterns, detect narrative consistency across channels through natural language processing, and flag urgency escalation sequences that manual analysis would miss.
Recommended Actions
Immediate steps: Map communication channels currently feeding security monitoring. Create basic SIEM rules for multi-channel sequences within 4-hour windows.
Implementation resources:
- MITRE ATT&CK techniques,
- NIST Cybersecurity Framework detection guidelines,
- Open-source SIEM templates,
- HTDR platforms,
- ISACs for campaign indicators.
Critical enhancement: Establish real-time alerting when high-value targets (executives, administrators, finance) receive multi-channel contact. These individuals warrant immediate verification regardless of message content.
Cross-channel correlation transforms security architecture from channel-specific monitoring to comprehensive campaign detection. Organizations that connect these dots detect sophisticated social engineering that single-channel defenses will always miss.